In the modern digital landscape, cybersecurity risk management is not just a technical necessity—it's a strategic imperative. As organizations increasingly depend on interconnected systems, cloud infrastructures, and sensitive data, the threat landscape continues to evolve. Cybersecurity risk management empowers organizations to proactively identify, evaluate, mitigate, and monitor cyber threats that could compromise their operations, data integrity, or business continuity.
Cybersecurity risk management (or cyber risk management) operates within the broader umbrella of enterprise risk management, but it zeroes in on IT security challenges and their potential impact on the business. A robust cyber risk strategy incorporates regular security assessments, sound policy creation, advanced security infrastructure, and continuous training for both IT and non-technical staff.

The Foundation: What Makes Cybersecurity Risk Management Effective
Cyber risk management becomes truly effective when it's an organization-wide initiative. It’s not merely an IT department's responsibility—it requires active collaboration among cross-functional teams, senior executives, the dedicated security team, and third-party vendors. When everyone is aligned, businesses can accurately identify threats, implement the right security tools, and adopt well-defined procedures to maintain a strong and responsive security posture.
Also read: What’s Next in Cyber Security? 10 Big Trends and Surprising Challenges in 2025
Why Cyber Risk Management is Crucial for Modern Organizations
Data is the lifeblood of contemporary businesses. From customer records and financial data to proprietary business intelligence, every byte of information has value—and vulnerabilities. Cyberattacks can block, alter, steal, or destroy this information, leading to major operational and reputational damage. Cyber risk management aims to do three things: anticipate where threats might occur, reduce their impact, and ideally, prevent them altogether.
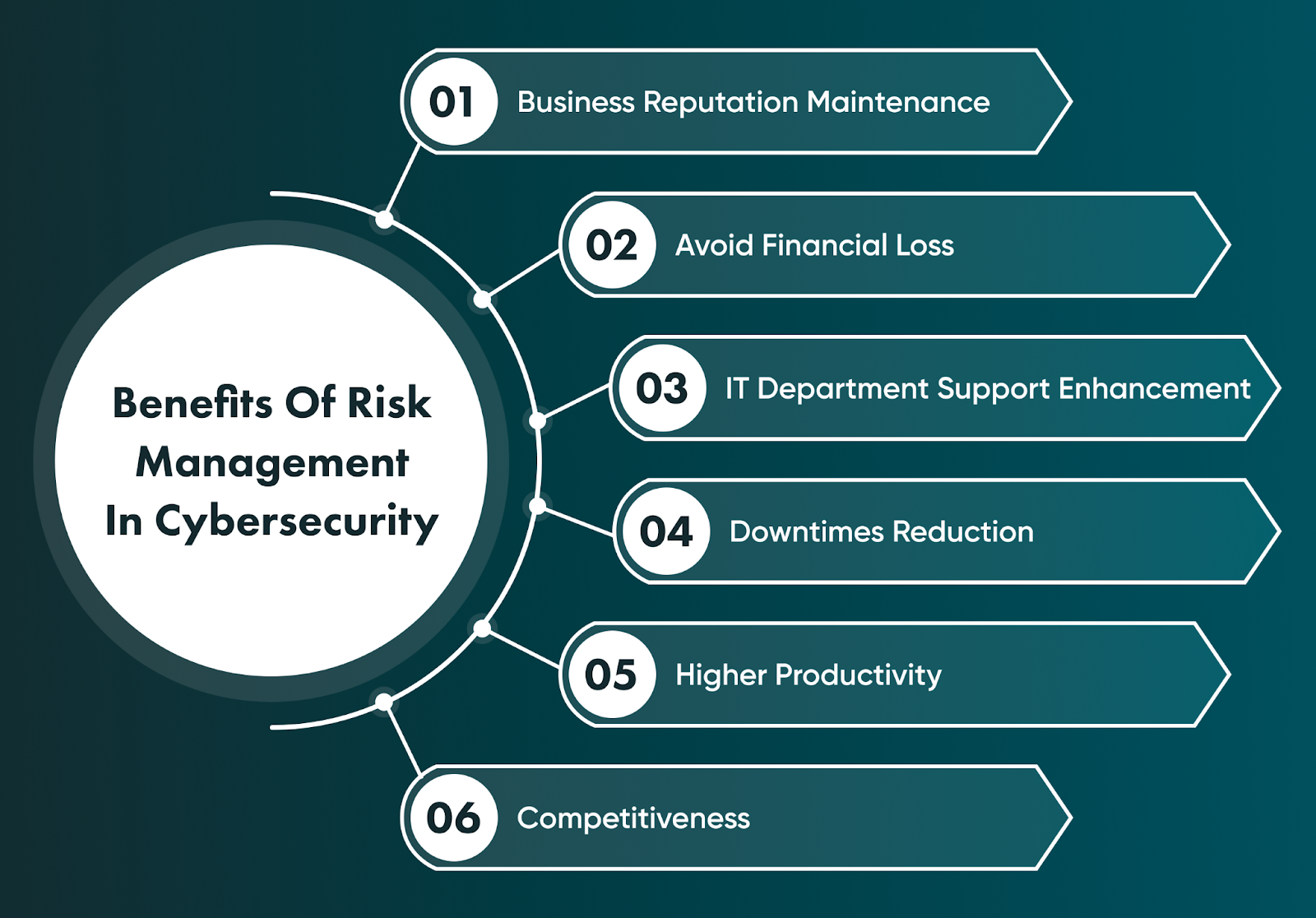
The tangible benefits of implementing a cybersecurity risk management program include:
-
Heightened Security Awareness: Risk assessments help uncover vulnerabilities, making it easier to implement changes in both infrastructure and behavior.
-
Prevention of Cyberattacks: From phishing and malware to ransomware and unauthorized access, cyber risk management reduces the likelihood and impact of attacks.
-
Business Continuity: A well-structured plan ensures that even during a breach, operations can continue with minimal disruption.
-
Regulatory Compliance: Many sectors operate under strict regulations requiring data protection. Risk management helps avoid breaches that could lead to fines or legal trouble.
-
Reputation Management: A successful cyberattack can erode trust among customers, investors, and partners. Prevention helps preserve brand integrity and customer loyalty.
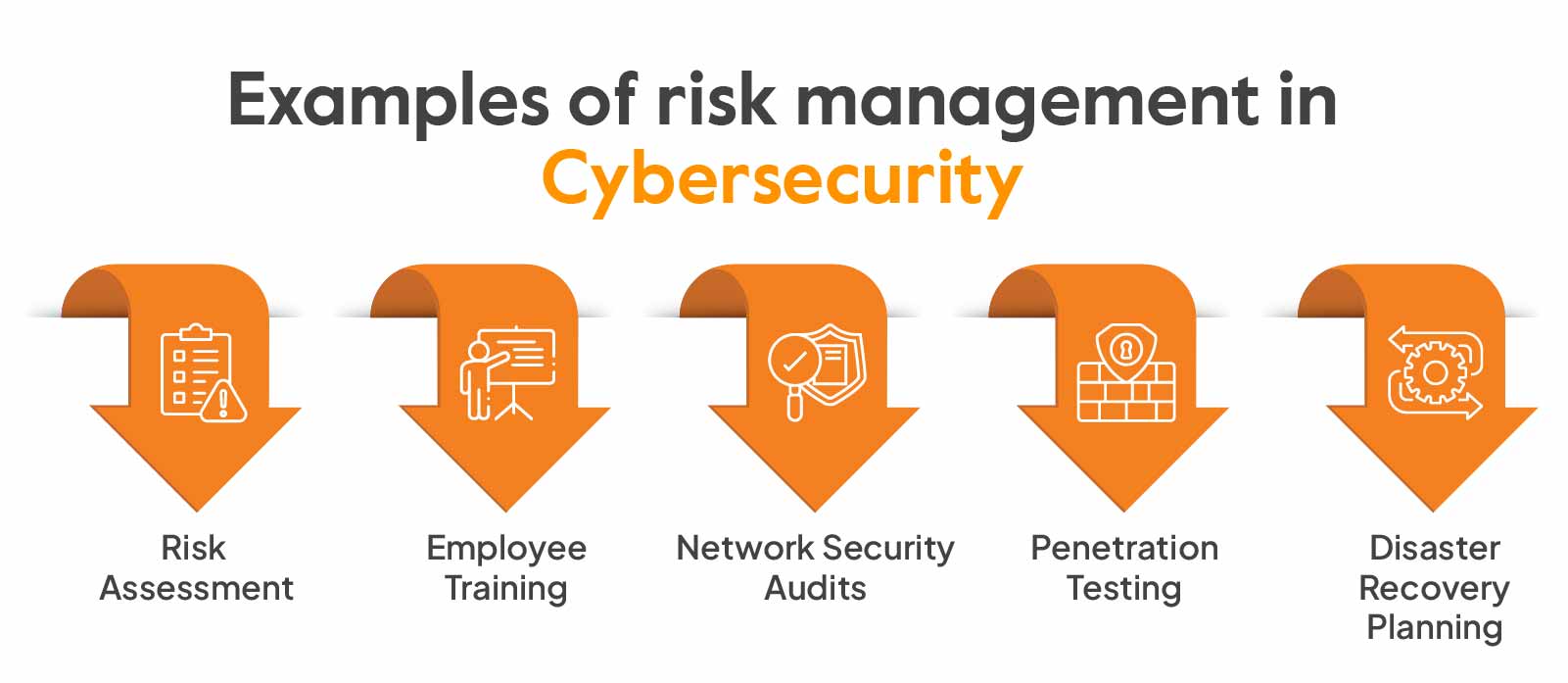
Core Components of a Cybersecurity Risk Management Strategy
Effective cyber risk management demands an end-to-end approach, encompassing everything from initial threat identification to incident response. The five foundational components include:
-
Risk Identification: This phase involves taking a complete inventory of IT assets—hardware, software, applications, and data—and identifying associated threats such as malware, insider threats, and misconfigurations. The goal is to recognize weak points before attackers do.
-
Risk Assessment: Once vulnerabilities are known, organizations must evaluate their severity. This involves analyzing the potential business disruption, regulatory implications, financial loss, and reputational damage associated with each vulnerability. Using risk quantification models helps in prioritizing threats by severity and likelihood of exploitation.
-
Risk Mitigation: After assessment, targeted controls are implemented to neutralize or reduce threats. These might include deploying new technologies (e.g., intrusion prevention systems), revising policies (e.g., zero-trust models), conducting regular staff training, and establishing robust incident response plans.
-
Risk Monitoring: Cybersecurity isn’t a one-and-done activity. Organizations must continuously monitor systems using real-time threat detection and alerting tools—often powered by AI. Frequent reviews and reports ensure the ongoing effectiveness of existing controls and help adapt to new threats.
-
Incident Response: When a threat bypasses defenses, an immediate and well-coordinated response is crucial. Incident response plans enable teams to contain damage, recover systems, and conduct post-mortems to refine future risk management strategies.
Choosing the Right Cybersecurity Risk Management Framework
A cybersecurity risk management framework acts as a blueprint for identifying and managing risks. However, no one-size-fits-all solution exists. The choice depends on an organization’s size, industry, existing compliance requirements, risk appetite, and internal capabilities.
Factors to Consider:
-
Understand Your Risks: Frameworks provide structure, but the responsibility to define business goals, identify vulnerabilities, and evaluate risks lies with the organization.
-
Business Alignment: The selected framework must align with unique business needs—like PCI DSS for companies processing credit card transactions or HIPAA for healthcare.
-
Expertise and Resources: Some frameworks require specialized skills. Selecting one that suits your team’s expertise can ease implementation and reduce training costs.
-
Avoid Duplication: If existing tools or controls are already in place, select a framework that complements rather than replicates them.
-
Customization and Metrics: Look for frameworks that allow customization and offer key performance indicators (KPIs) to objectively measure risk management performance.
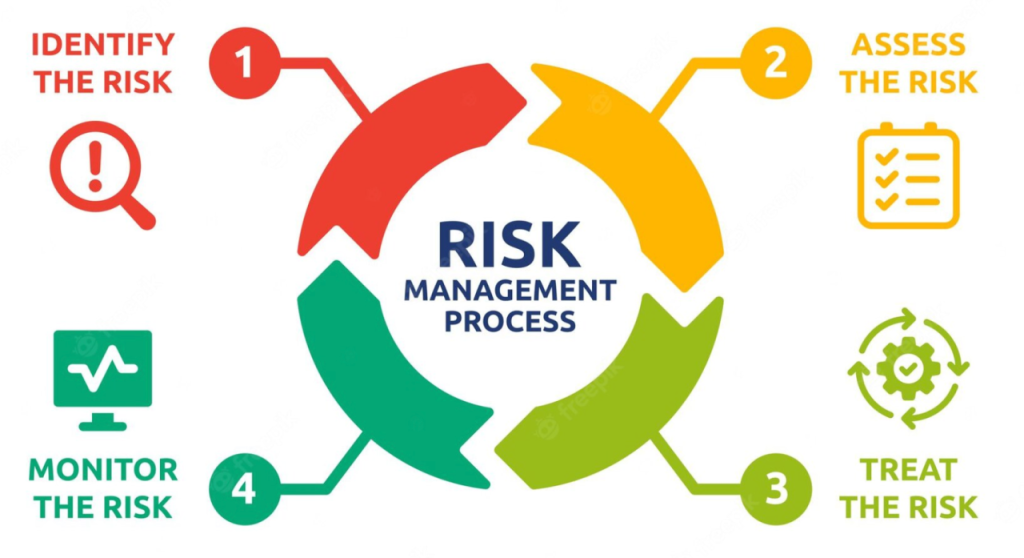
Common Cybersecurity Risk Management Frameworks
A variety of established frameworks help organizations structure their cybersecurity risk strategies:
-
NIST Cybersecurity Framework (CSF): A flexible, voluntary framework that revolves around five core functions—Identify, Protect, Detect, Respond, and Recover. It’s suitable for a broad range of industries.
-
ISO/IEC 27001 and 27002: Internationally recognized standards for establishing and maintaining information security management systems.
-
COBIT: Focused on IT governance, COBIT helps align cybersecurity initiatives with broader business goals.
-
CIS Controls: Developed by the Center for Internet Security, this framework provides 18 prioritized best practices for bolstering cyber resilience.
-
FAIR (Factor Analysis of Information Risk): Converts complex cyber risks into quantitative data, helping leadership understand their financial implications.
-
COSO ERM: A broader enterprise risk management framework that includes cyber risks among all other business risks.
-
RMM (Risk Maturity Model): Offers a maturity-based self-assessment to benchmark current capabilities against a five-level scale, from Ad-Hoc to Leadership.
Other industry-specific or regionally mandated frameworks include HIPAA, HITRUST (for healthcare), FERPA, COPPA (for education), PCI DSS (for payments), and GDPR or Cyber Essentials (for organizations in the EU and UK).
Best Practices for Cybersecurity Risk Management
No matter the framework or industry, several universal best practices enhance the effectiveness of any cyber risk management effort:
-
Think Like an Attacker: Stay ahead by understanding how attackers operate. Use threat intelligence and simulated attacks to expose hidden vulnerabilities.
-
Adopt Zero-Trust: Assume no one is automatically trustworthy. Implement strict access controls and enforce least-privilege policies.
-
Document Everything: Security policies and procedures must be clearly documented and communicated to all employees and third parties.
-
Comprehensive Monitoring: Employ robust monitoring tools with anomaly detection, real-time alerts, and user behavior analytics.
-
Rapid Response: Leverage AI and automation for real-time mitigation. Quick responses often mean the difference between a minor event and a catastrophic breach.
-
Continuous Testing: Simulate attacks, test backups, and evaluate incident response plans regularly. Stay ahead of evolving threats by updating policies and systems accordingly.
-
Blame-Free Post-Mortems: Following an incident, focus on understanding and improving—not blaming. A constructive approach helps uncover issues and strengthens defenses.
-
Ongoing Education: Cybersecurity is everyone's job. Implement continuous training so every team member understands their role and the consequences of failure.
Integrating Cybersecurity into Enterprise Risk Management (ERM)
Cyber risk management should not exist in a silo. It must be embedded within an organization’s broader enterprise risk management strategy:
-
Build on a Strong ERM Foundation: Clearly define risk tolerance and establish governance structures with well-outlined roles and responsibilities.
-
Achieve Strategic Alignment: Cybersecurity goals should support overall business objectives and reflect the same risk priorities as those outlined in ERM.
-
Speak in Business Terms: Frame cyber risks in terms of financial, operational, or legal impact to engage executive stakeholders more effectively.
-
Unified Response Plans: Sync incident response with business continuity plans to ensure seamless, organization-wide handling of disruptions.
-
Update Regularly: ERM reviews should trigger cyber risk reassessments, ensuring that both remain current and aligned with emerging threats.
-
Use Integrated Frameworks: Adopt ERM-focused frameworks like COSO ERM, NIST CSF, or ISO 31000, which naturally incorporate cybersecurity into the enterprise-wide risk posture.
Cybersecurity risk management is no longer a reactive function—it’s a proactive, strategic element of successful digital businesses. From protecting sensitive data and maintaining customer trust to ensuring legal compliance and operational resilience, the value of a well-implemented cyber risk program cannot be overstated. By adopting the right frameworks, aligning with enterprise goals, and adhering to best practices, organizations can navigate an increasingly complex threat landscape with confidence and clarity.
With inputs from agencies
Image Source: Multiple agencies
© Copyright 2025. All Rights Reserved Powered by Vygr Media.